What We Can Learn From The Recent News About the Unknown Future of MITRE’s CVE Database
Over the last several days, we have received a lot of inquiries from customers and partners about the recent news on the unknown future of the MITRE National Vulnerability (NVD) database. It is another reminder that in today’s rapidly evolving cybersecurity environment, organizations cannot afford to rely on a single stream of intelligence. It also demonstrates why platforms that aggregate multiple intelligence sources are more critical than ever.
When Critical Vulnerability Information Sources Are at Risk
We tend to think about supply chain disruptions related to physical goods, but this is a wake up call that information supply chains are equally important to consider.
So what happened? On April 15, 2025, a memo indicated that MITRE’s contract to support CVE (Common Vulnerabilities and Exposures) and related programs was set to expire on April 16, 2025. Fortunately, by 9am EDT on April 16, the MITRE contract had reportedly been renewed, and there would be no actual impact or interruptions to vulnerability intelligence services for at least a year- beyond that year is still unknown. While this raised immediate concerns across the cybersecurity community, it also illustrated the importance of diversified vulnerability intelligence sources.
Why Multi-Source Vulnerability Intelligence Matters
The MITRE situation perfectly exemplifies why organizations need robust, multi-source intelligence platforms rather than a dependency on single sources, namely:
Resilience Against Source Disruptions
When a key intelligence source experiences disruption, organizations with diversified sources can maintain operational continuity.
Comprehensive Coverage
Different intelligence sources often capture different aspects of vulnerabilities. Vendor advisories might contain details not yet reflected in the National Vulnerability Database (NVD).
Timely Intelligence
Multiple sources allow for earlier detection of vulnerabilities, as information often appears in specialized forums or vendor bulletins before being officially cataloged.
Contextual Richness
By aggregating multiple intelligence streams, organizations gain a more nuanced understanding of vulnerabilities, including real-world exploitation status.
The Evolving Information Supply Chain
The cybersecurity intelligence landscape has been undergoing a fundamental transformation for some time. In fact, this is the very reason Recorded Future was formed as a company nearly 15 years ago. Centralized information sources need to be complemented by a distributed network of intelligence mirroring the world. This shift represents a new paradigm in how security intelligence flows:
From Centralized to Distributed
Organizations are moving away from reliance on single, authoritative sources toward networks of complementary intelligence.
From Reactive to Proactive
Multi-source intelligence enables earlier detection and faster response to emerging threats.
From Generic to Contextual and Precise
Diverse sources provide richer context, allowing for more precise risk assessment tailored to specific organizational environments.
Practical Steps for Security Teams
For security professionals, this shift necessitates adjustments in vulnerability management workflows:
Diversify CVE Sourcing for Vendor Risk Ratings
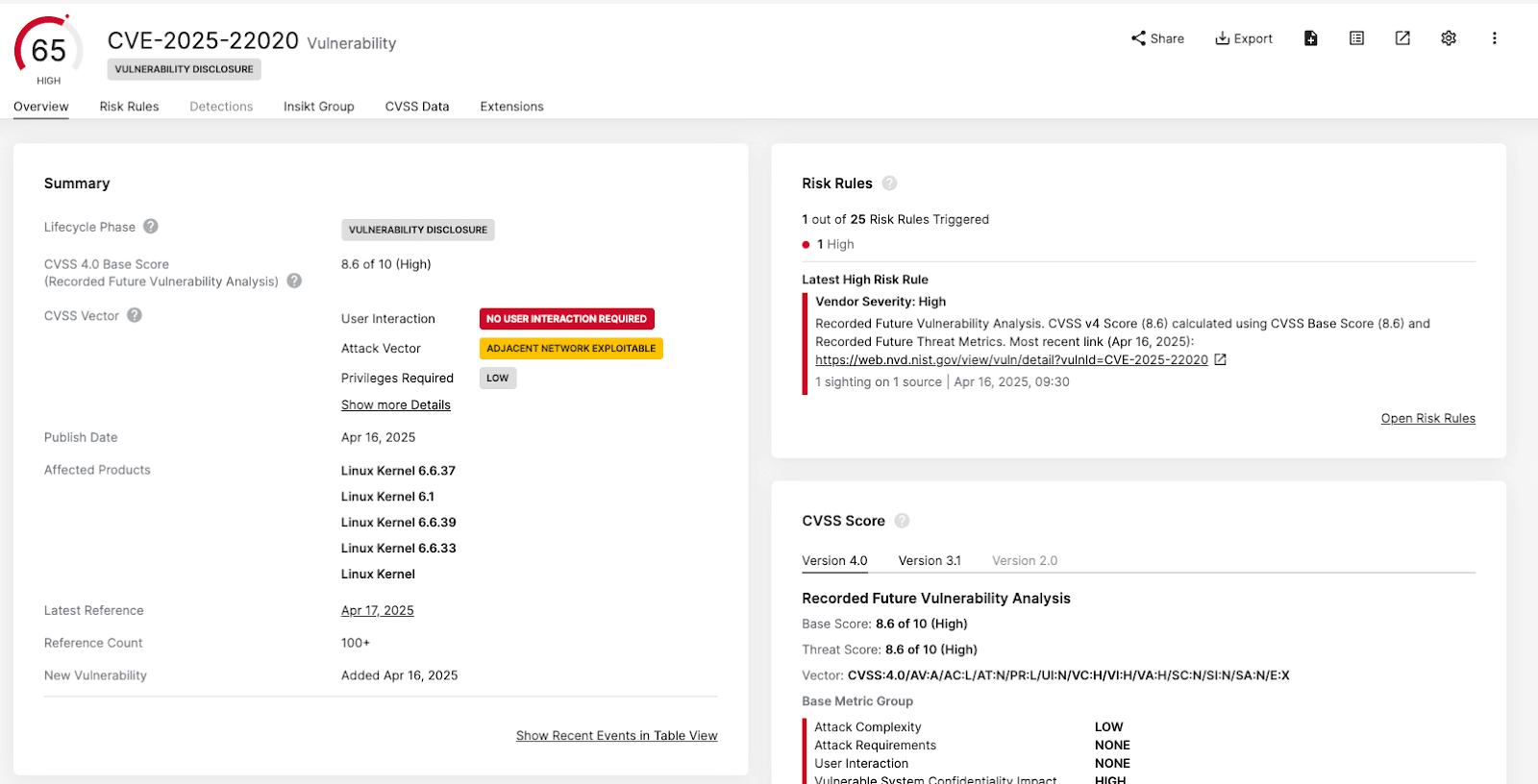
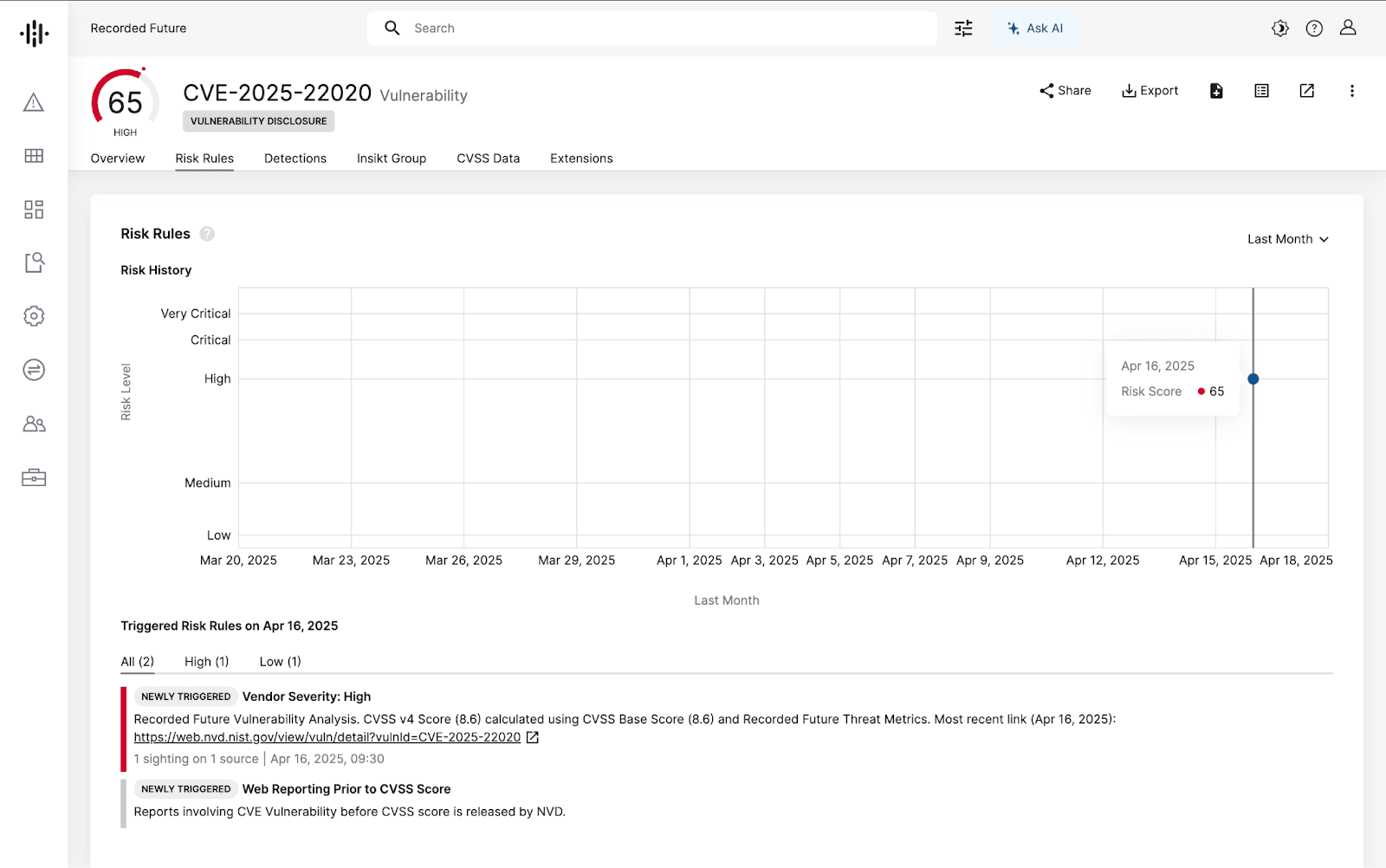
Recorded Future automates risk alerting and tracking, including CVEs by severity. Beyond MITRE NVD’s CVSS scores, we incorporate proprietary and open source scoring and data. This has enabled us to alert on vulnerabilities, an average of 11 days, before NVD even computes their risk scores, as exemplified in the screenshot from our platform.
_
The screenshot from our platform below of a Recorded Future alert captured before NVD scoring – providing early warning signals of potential risk._
Evaluate Source Dependencies
Review current intelligence sources to identify potential single points of failure in your security information supply chain.
Implement Resilient Workflows
Design vulnerability management processes that can adapt to changes in intelligence sources without operational disruption.
Know How to Action the Data
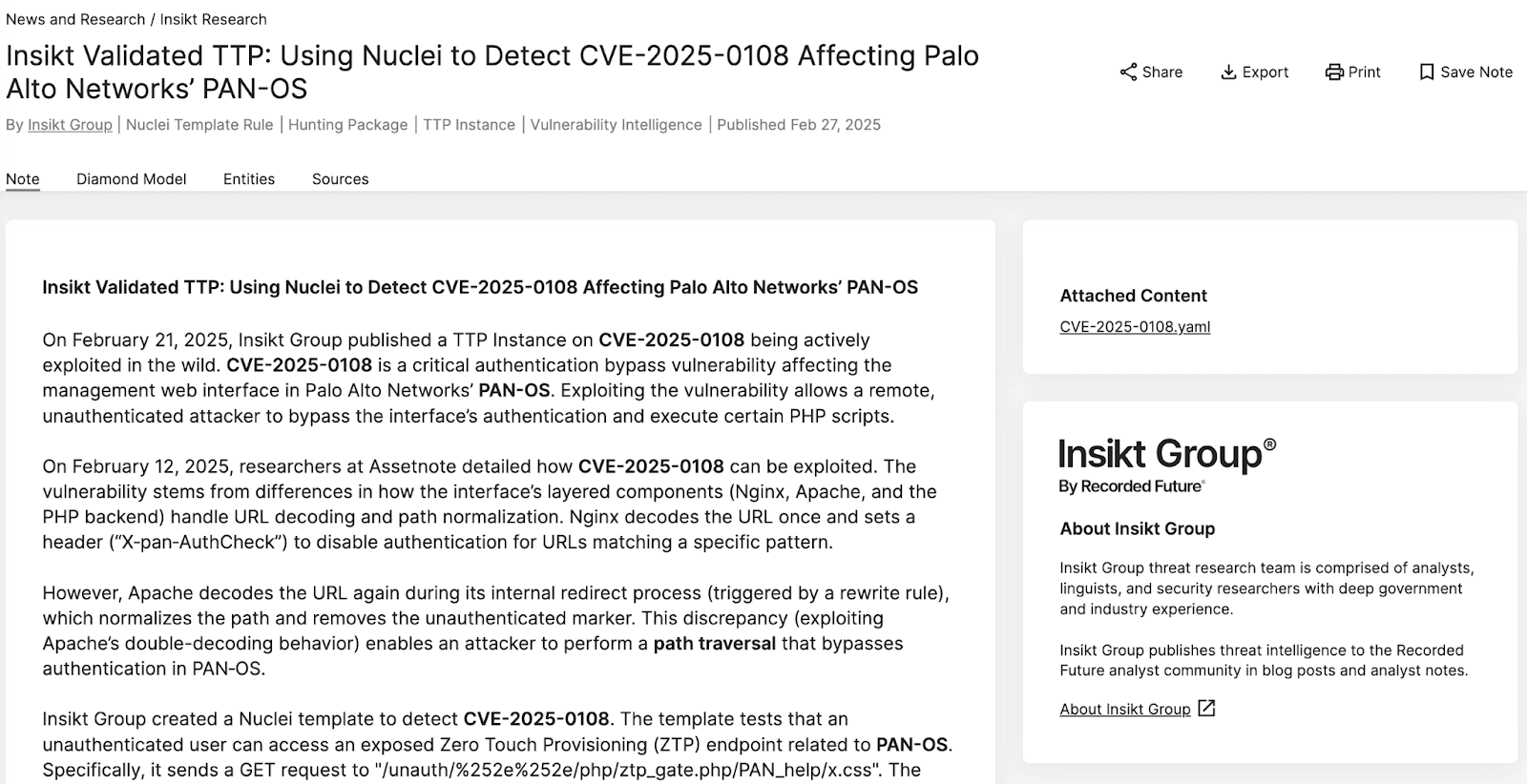
Having a robust and resilient information supply chain is important, but equally important is knowing what to action on and how to do it. Actionable intelligence is the only intelligence that matters. Organizations require additional detail on the exposures and tactics along with specific threat hunting packages. (See screen shot below of a TTP validated by our Insikt group research team along with the attached YAML threat hunt package to eradicate it.)
Conclusion: The Power of Intelligence Integration
The recent MITRE contract situation serves as a timely reminder that in cybersecurity intelligence, diversity and integration are strengths. It is very likely that additional community and open sources will emerge to expose and track this information, which will be great incremental sources. Organizations that leverage platforms capable of aggregating, normalizing, and contextualizing intelligence from multiple sources gain significant advantages in risk identification, prioritization, and mitigation. They are also more protected from disruptions related to any one particular source. This is supply chain management 101.
Even better is when the platform can automate and proactively take action based on a wide variety of intelligence sourcing. As information supply chains continue to evolve, the most resilient security postures will belong to those organizations that embrace multi-source intelligence platforms—ensuring that when one source experiences disruption, the flow of critical security intelligence and automation continues uninterrupted.
Recorded Future will continue help on this mission in every way we can. In addition to CVE information, we track over 4,000 threat actors, including 430 nation-state sponsored groups, and a variety of other sources of threats used in our analysis and recommendations. We actively monitor more than 90,000 command and control servers while scanning 30 million domains and URLs each day. We make some of this available for free in our public vulnerability database site, where you can see trending vulnerabilities and search for CVEs and software: https://www.recordedfuture.com/vulnerability-database