Check out NIST’s effort to further mesh its privacy and cyber frameworks. Plus, learn why code-writing GenAI tools can put developers at risk of package-confusion attacks. Also, find out what Tenable webinar attendees said about identity security. And get the latest on the MITRE CVE program and on attacks against edge routers.
Dive into five things that are top of mind for the week ending April 18.
1 – NIST updates Privacy Framework, tailoring it to the Cybersecurity Framework and adding an AI section
Recognizing the data protection and cyberattack prevention overlap and are deeply intertwined, the U.S. government is aligning two foundational privacy and cybersecurity frameworks.
This week, the U.S. National Institute of Standards and Technology (NIST) released a draft update of its Privacy Framework (PFW) that more closely interconnects it with the popular Cybersecurity Framework (CSF), which was updated in 2024.
Although the PFW can be used on its own, this updated version makes its use with the CSF “seamless” so that organizations can leverage the two frameworks “to manage the full spectrum of privacy and cybersecurity risks,” Julie Chua, Director of NIST’s Applied Cybersecurity Division, said in a statement.
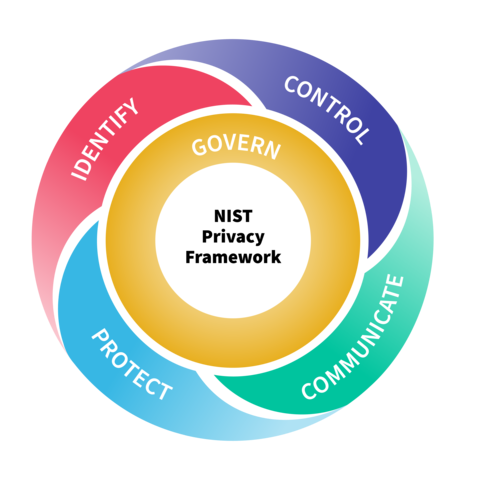
Both frameworks have a “Core” section, which outlines detailed activities and outcomes aimed at helping organizations discuss risk management. “The PFW 1.1 Public Draft Core is realigned with the CSF 2.0 Core in many places, making life easier on users,” NIST said in the statement.
The “NIST Privacy Framework 1.1 Initial Public Draft” also adds a new section about the risks to data privacy from artificial intelligence. Specifically, organizations can use it to “ensure that organizational privacy values are reflected in the development and use of AI systems,” the PFW draft reads.
NIST first published the PFW in 2020, with the goal of helping organizations mitigate the privacy risks associated with the processing of personal data in their computer systems. It outlines five core functions:
- Identify, which includes inventorying the organization’s data-processing scenarios and conducting privacy risk assessments
- Govern, which involves the creation and adoption of the organization’s governance structure for data privacy
- Control, which addresses the organization’s development and implementation of appropriate data-management activities
- Communicate, which includes sharing publicly how the organization processes personal data and manages privacy risks
- Protect, which touches on the organization’s data security processes aimed at preventing cyber breaches
The PFW 1.1 draft is open for public comment until June 13, 2025. NIST plans to publish a final version later this year.
For more information about data privacy and data security, check out these Tenable resources:
2 – GenAI code-generation hallucinations open the door for package-confusion attacks
Here’s a warning for developers who use generative AI to write code: Generative AI tools may prompt you to download software packages that are infected with malware.
That’s the main finding from the study “We Have a Package for You! A Comprehensive Analysis of Package Hallucinations by Code Generating LLMs” by researchers from the University of Texas at San Antonio, the University of Oklahoma and Virginia Tech.
How can this happen? When prompted to write code, generative AI tools powered by large language models (LLMs) often suggest that developers download software packages from public repositories.
However, in many cases, the software packages the generative AI tools mention don’t exist. The tools invent names for non-existent software packages and falsely say the packages are located in specific software repositories.
Best case scenario is that the developer goes looking for the imagined software package and doesn’t find it. Unfortunately, cyberattackers are taking note. They’re baptizing their malicious packages with the made-up names and storing them in repositories, hoping developers will inadvertently download them thinking they’re legit.

“These hallucinations, which arise from fact-conflicting errors when generating code using LLMs, represent a novel form of package confusion attack that poses a critical threat to the integrity of the software supply chain,” the researchers wrote.
The researchers generated 576,000 code samples in Python and JavaScript using 16 generative AI tools and two unique prompt datasets. Here are some key findings:
- The incidence of package hallucination was an average of 5.2% for commercial tools and 21.7% for open-source tools.
- The tools generated about 205,000 unique hallucinated package names.
“Our experiments and findings highlight package hallucinations as a persistent and systemic phenomenon while using state-of-the-art LLMs for code generation, and a significant challenge which deserves the research community’s urgent attention,” the researchers wrote.
The researchers also tested several mitigation techniques that helped reduce the incidence of software-package hallucinations, including retrieval augmented generation; self refinement; and fine tuning.
For more information about AI security and the risks of using generative AI for writing code:
3 – Tenable polls webinar attendees on identity security
During our recent webinar “Three Reasons Why It’s Time to Embrace Identity as Part of Exposure Management,” we polled attendees about identity security topics, such as their ability to correlate identity incidents with broader attack paths. Check out what they said.
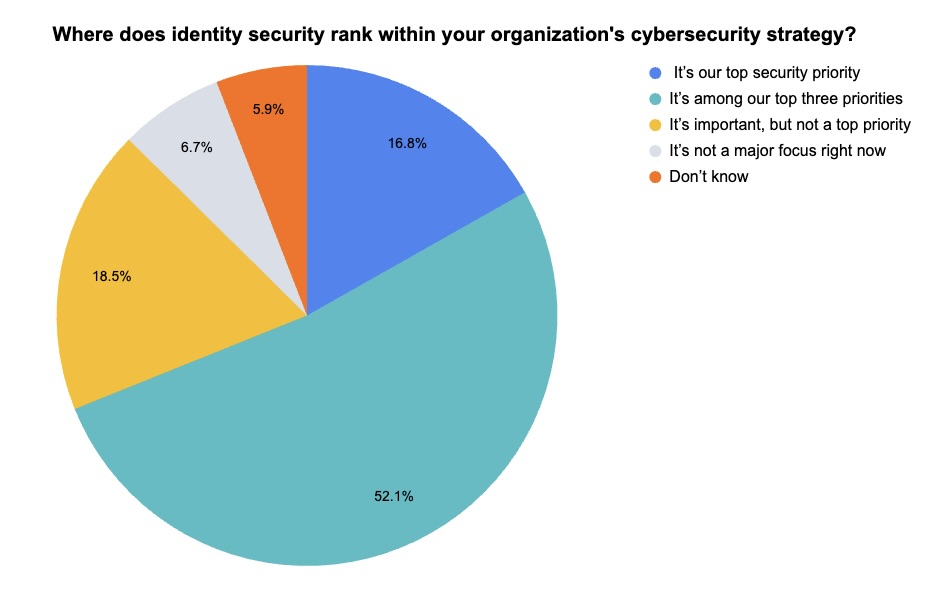
(119 webinar attendees polled by Tenable, March 2025)
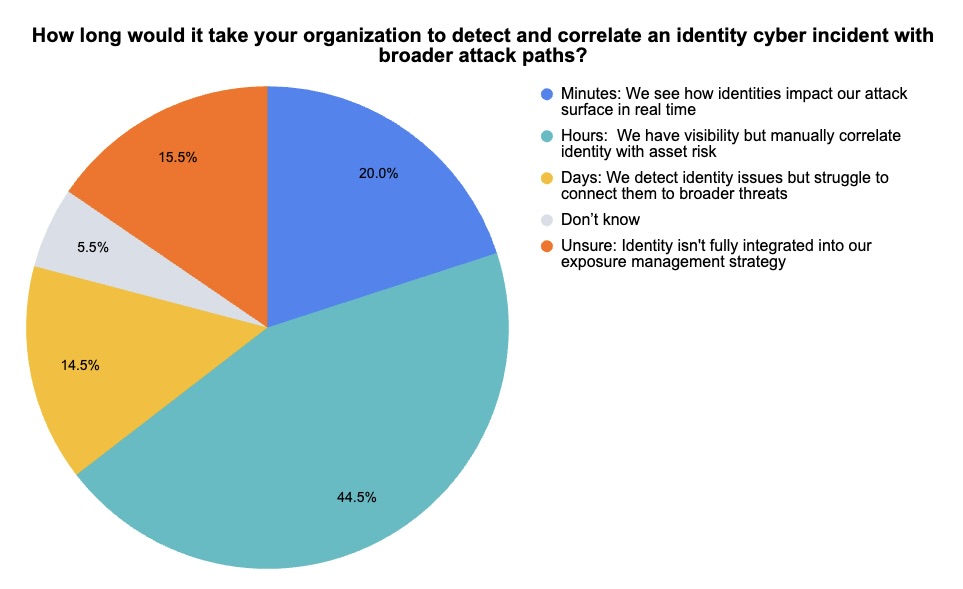
(110 webinar attendees polled by Tenable, March 2025)
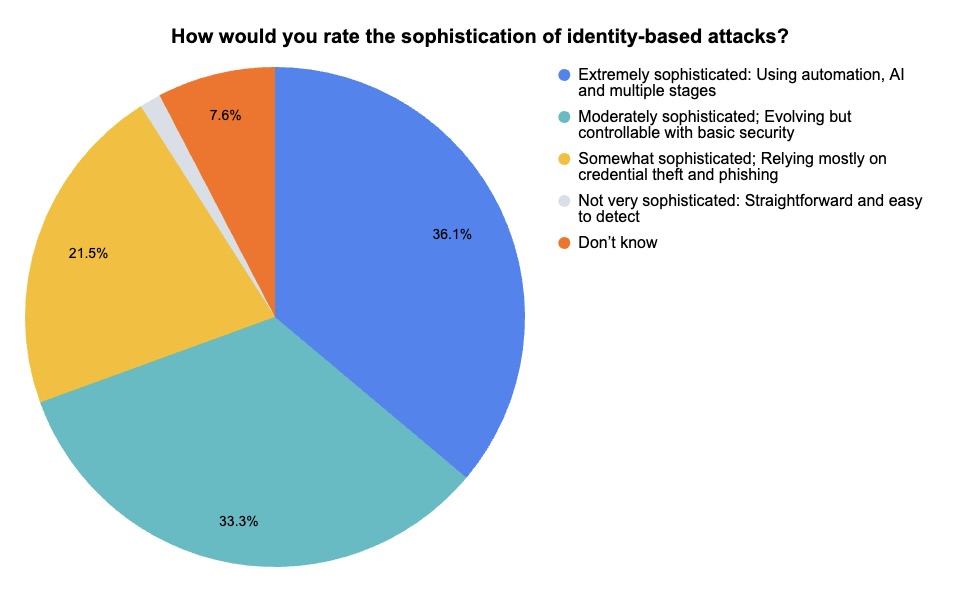
(144 webinar attendees polled by Tenable, March 2025)
Check out this on-demand webinar to learn how you can adopt a more proactive identity security strategy as part of your exposure management program.
4 – Canada’s cyber agency warns about spike in router hacking
Nation-state attackers associated with China’s government, including the cyber espionage group Salt Typhoon, are ramping up attacks on network edge routers of critical infrastructure organizations.
The Canadian Centre for Cyber Security issued the warning this week via an advisory titled “People’s Republic of China activity targeting network edge routers: Observations and mitigation strategies” which details the threat and offers mitigation recommendations.
Compromised network edge routers can allow attackers to breach a network and then monitor, modify, and exfiltrate network traffic, and even move deeper into the victim’s network, according to the advisory.
A key insight: The attackers are feasting on low-hanging fruit — misconfigured and unpatched routing devices. The best and simplest prevention? Patch these products as soon as possible.

“Threat actors often compromise network perimeter defenses by exploiting known vulnerabilities in edge devices. These security weaknesses are usually already identified, and patches are available to fix them. However, breaches occur because these patches are not consistently applied or implemented in a timely manner,” the advisory reads.
The Cyber Centre has also observed router compromises stemming from basic security mistakes, such as the use of default and weak passwords, and of default security settings.
Other mitigation recommendations include:
- Disable unnecessary network edge services, especially unsecured ones such as HTTP.
- Remove direct internet access to device management interfaces, restricting admins to internal and secure management networks.
- Protect all administrative access with phishing-resistant multi-factor authentication.
- Use modern encryption standards.
- Keep firmware updated.
- Adopt secure, centralized logging, encrypt logging traffic and store logs offsite.
For more information about Salt Typhoon:
5 – CVE program renewed for one year, but questions about its future linger
A collective gasp was heard around the cybersecurity world on Tuesday, when news broke that the MITRE Common Vulnerabilities and Exposures (CVE) program might be in imminent danger of shutting down.
Fortunately, this scenario didn’t materialize, after the U.S. Cybersecurity and Infrastructure Security Agency (CISA) came to the rescue and extended the program’s funding for one year just as it was set to expire.

Naturally, concerns remain about the MITRE CVE program and the critical services it provides, given the close call it experienced and the limited one-year extension it obtained.
Speaking to The Wall Street Journal, Tenable Chief Security Officer and Head of Research Bob Huber said efforts to reform the CVE program will likely yield a public-private partnership of some sort.
“Most of the companies that operate in this place are well-known amongst each other, as are the people responsible for those programs. I think there’s an opportunity here to improve that partnership and spread the responsibility,” Huber told the Journal.
As of the end of 2024, the CVE program had published more than 250,000 CVEs. Launched in 1999, the CVE program provides a foundational, common taxonomy for tracking vulnerabilities and exposures.
To get all the details and insights about this issue, check out these two Tenable blogs:
