Overview
During security testing, Rapid7 discovered that Konica Minolta bizhub 227 Multifunction printers (MFPs) were vulnerable to a pass-back attack. The affected products identified were:
This issue has been assigned the following CVEs:
Product description
The Konica Minolta bizhub Multifunction printer (MFP) is an all-in-one enterprise printer designed to deliver print, copy, scan, fax, and email capabilities for enterprise business environments.
Credit
The pass-back vulnerabilities in the Konica Minolta bizhub MFPs were discovered by Deral Heiland, Principal IoT Researcher at Rapid7. After coordination with the vendor, this disclosure is being published in accordance with Rapid7’s vulnerability disclosure policy.
Exploitation and remediation
This section details the potential for exploitation and remediation guidance for the issues discovered and reported by Rapid7, so that producers of this technology can gauge the impact of these issues appropriately and develop mitigations.
Pass-back attack Via LDAP (CVE-2025-6081)
While examining the Konica Minolta bizhub 227 MFP device, Rapid7 found that the MFP device was vulnerable to a Pass-Back Attack. A Pass-Back attack is a vulnerability that allows a malicious actor to reconfigure a MFPs device’s external services, such as LDAP, to point to another external system which is controlled by the malicious actor. So, when that LDAP authentication is requested, the malicious actor can then capture the services access credentials.
If a malicious actor gains access to the Lightweight Directory Access Protocol (LDAP) configuration page and the LDAP services are configured for authentication, the malicious actor can then reconfigure the LDAP service’s IP address (Figure 1) to point to a device they control, without being required to change the LDAP password setting.
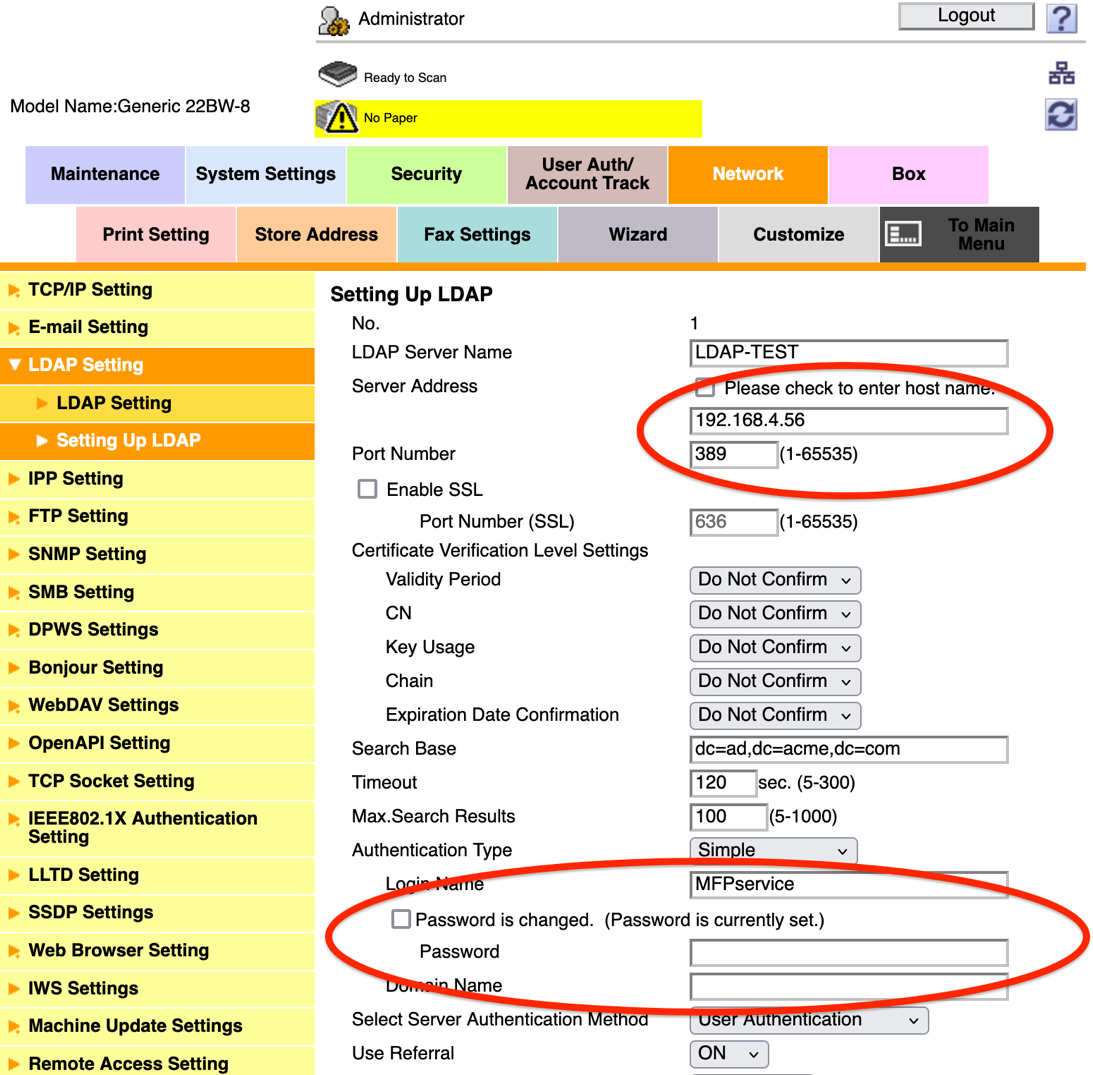
Figure 1: Change LDAP server IP address
Once the LDAP IP address has been changed, and saved, a malicious actor can then click on “Check Connection” (Figure 2) to trigger the MFP to test the LDAP login.
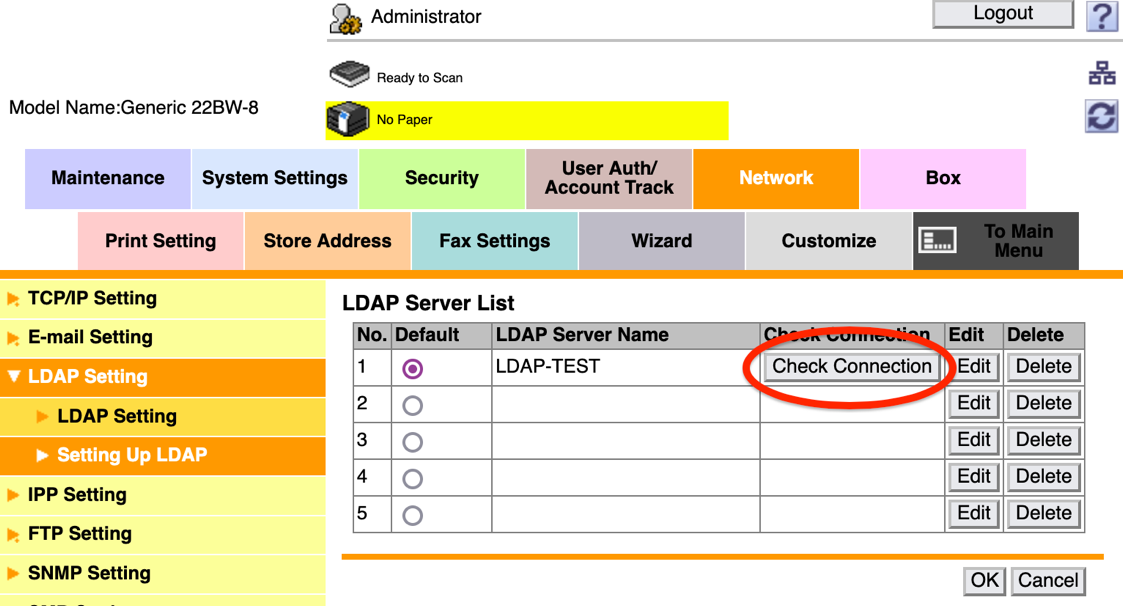
Figure 2: Click Check Connection
By running a LDAP port listener (Metasploit auxiliary/server/capture/ldap) on a host that the malicious actor controls, they are then able to capture the clear text LDAP service credentials as shown below in Figure 3. This attack requires access to the MFP printer admin account, and LDAP services must have been configured for normal operation to a valid LDAP server.
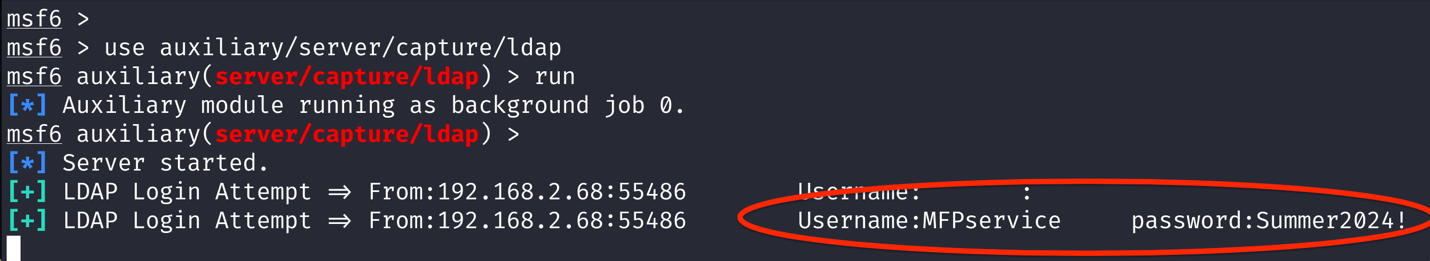
Figure 3: Capture Clear Text account with Metasploit LDAP Listener
Impact
If a malicious actor can successfully leverage these issues, it would allow them to capture credentials for Windows Active Directory. This means they could then move laterally within an organization’s environment and compromise other critical Windows servers and file systems.
Remediation guidance
Organizations leveraging Konica Minolta bizhub MFP devices should set a complex password for the Admin account, and also avoid using LDAP authentication accounts which have elevated access rights. Additional details are available in the vendor advisory.
Disclosure timeline
May 7, 2024: Rapid7 contacts vendor to disclose vulnerability.
May 7, 2024 – May 14, 2024: Konica Minolta acknowledges receipt of disclosure. Rapid7 shares vulnerability details. Vendor confirmed receipt of disclosure writeup.
May 22, 2024: Konica Minolta provides update of remediation progress.
August 2, 2024: Konica Minolta replies, unable to provide ETA for when a fix will be ready.
October 24, 2024: Rapid7 requests an ETA on fixes.
November 10, 2024: Konica Minolta provides update of planned firmware release for June 2025.
June 4, 2025: Rapid7 informs Konica that with no disclosure date in place, and with repeated lapses in previously stated disclosure dates, Rapid7 will publish their advisory on June 30, 2025.
June 30, 2025: This disclosure.
