Executive Summary
On April 19, 2025, Recorded Future® Payment Fraud Intelligence identified lidlorg[.]com as a likely purchase scam website that employs brand impersonation against a German international discount retailer. As of May 8, 2025, our analysis has linked lidlorg[.]com to a network of 71 likely purchase scam websites, including others that combine brand impersonation and online ad campaigns for propagation. All identified scam websites use one or more of twelve shared merchant accounts to process visitor transactions. All transactions with these merchant accounts are highly likely to be fraudulent and facilitate card compromise.
Purchase scams present financial fraud risks to card issuers and compliance risks to merchant acquirers, especially in cases where linked scam merchant accounts are also abused to support transaction laundering activity. To reduce these risks, card issuers should take action against identified merchant accounts and card accounts that have transacted with those merchants, while merchant acquirers should take action against the merchant accounts. We describe these mitigation strategies in detail in the Mitigations section of this report.
Key Findings
- On April 19, 2025, we identified lidlorg[.]com as a likely purchase scam website that uses brand impersonation against a German retailer.
- The scam website lidlorg[.]com is likely part of a network of 71 purchase scam domains using the same merchant accounts to defraud victims and steal victim data.
- Transactions with the merchant accounts linked to lidlorg[.]com are highly likely to be fraudulent and facilitate card compromise. These merchant accounts include AKRU KERAMIK GMBH, ANTONLINE E-COMMERCE STO, BALSAMIC, CLOTHWEARABLY, LMS AESTHETICS, MYCOZYBABIES, ONCLOTHESSHOES, PETHOUSEN LLC, REFINEDHAT, YSPCLOTHINGGSHOP, YSPNIHILSTOOL, and YSPQHWLKJSHOP.
- It is unclear whether the network of scam domains and merchant accounts is controlled by a single threat actor or various threat actors acting in concert — for example, through partnership on the dark web and the provision of dark web-based services in a greater scam ecosystem.
- To attribute this scam network to a single threat actor or various threat actors, card issuers and merchant acquirers with access to merchant data can likely leverage commonalities in associated merchant registration information, such as company data.
Threat Analysis of Purchase Scam Websites
On April 19, 2025, Recorded Future identified lidlorg[.]com as a likely purchase scam website. The operators of lidlorg[.]com employed brand impersonation targeting a German international discount retailer chain, as indicated by the use of typosquatting in the domain name and the abuse of a brand logo by “EU STORE” and “L Clearance”, two advertiser accounts linked to lidlorg[.]com (Figure 1). The scam website likely defrauds victims through the use of three linked merchant accounts, which enable the operator to conduct a fraudulent scam transaction while stealing victim personal and financial data for downstream fraud.
Recorded Future Payment Fraud Intelligence distinguishes purchase scam websites from phishing websites through their use of linked merchant accounts. While the purchase scams we identify are similar to other online scams (especially in their reliance on fraudulent offers for goods and services that buyers will never receive), they are distinct from phishing websites because they can process victim payments rather than simply collecting victim data through bogus form submissions.
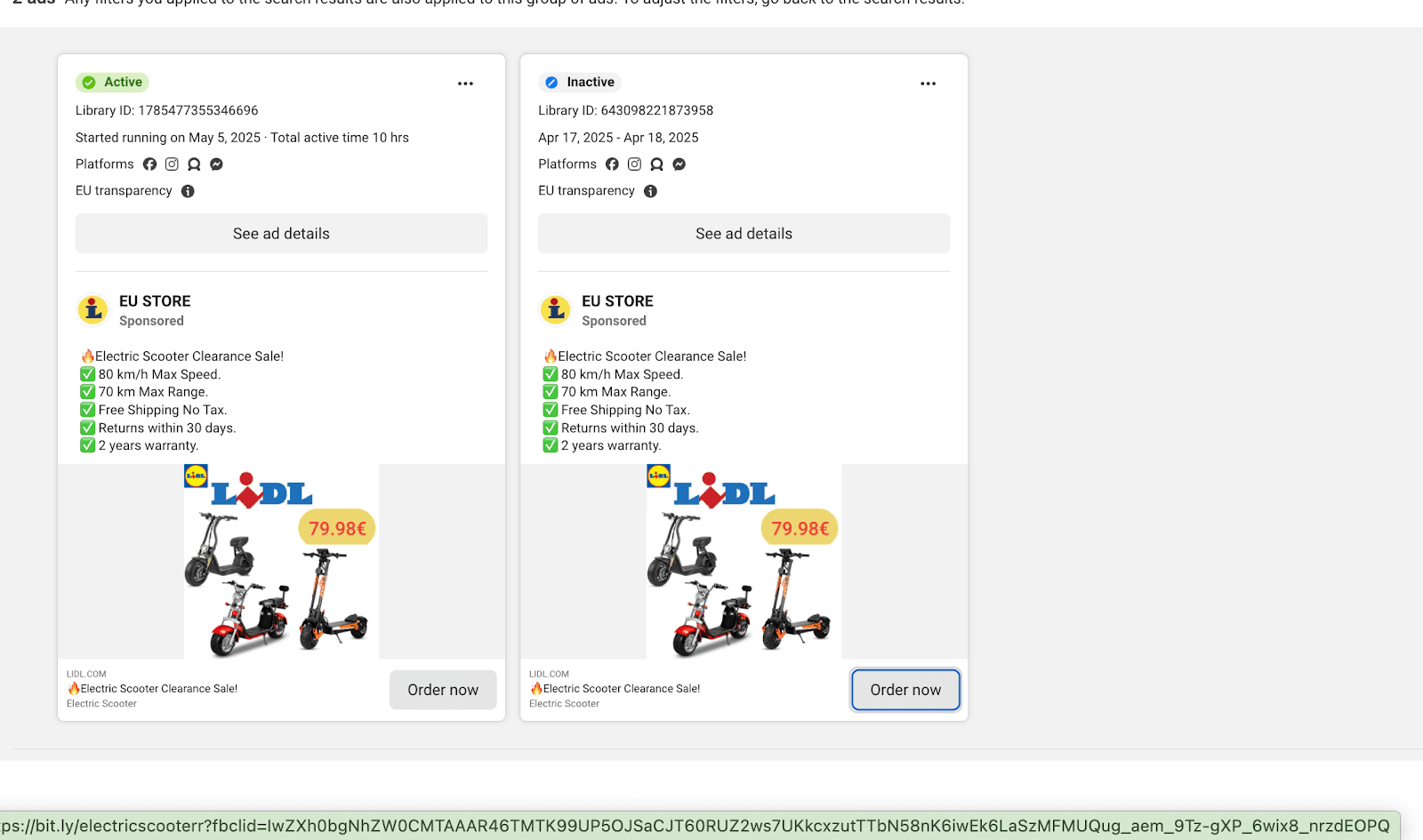
Figure 1: Online ad accounts for the likely scam website lidlorg[.]com impersonate a German brand (Source: Facebook Ads)
Our analysis indicated that lidlorg[.]com is part of a network of 71 likely scam e-commerce domains, as indicated by overlapping use of scam merchant accounts. All likely scam domains use various combinations of the same merchant accounts for their payment functionality and have been operational since no later than February 2025. Many of the domains also use typosquatting to impersonate multiple brands. At the time of our analysis, many of the domains were associated with active or historical online ad campaigns. Many of these were also removed by the ad platform for “Unacceptable Business Practices,” which includes scam activity. On average, the domains were 65 days old and likely malicious, as indicated by their average DomainTools risk score of 88/100.
Figure 2 illustrates the links between the identified scam domains and merchant accounts. The Appendix of this report lists the scam domains, merchant accounts, and all timestamps when we confirmed that they were linked.
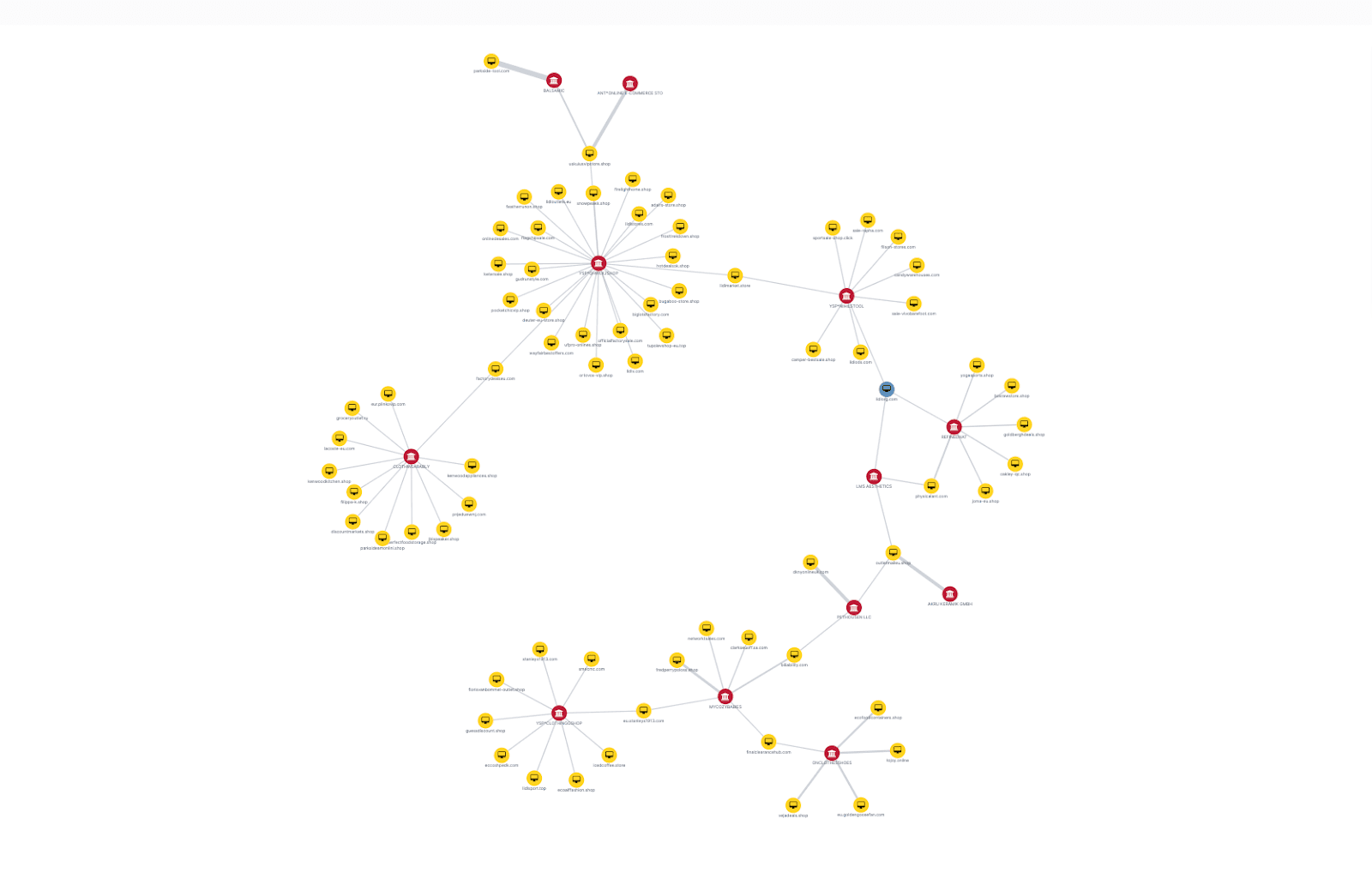
Figure 2: This graph demonstrates the overlapping use of eight merchant accounts by 71 scam domains; lidlorg[.]com, the “patient-zero” domain within the investigation, is graphed in light blue (Source: Recorded Future)
Transactions with merchant accounts linked directly or indirectly to lidlorg[.]com are highly likely to be fraudulent and facilitate card compromise. As of May 8, 2025, lidlorg[.]com has directly used three merchant accounts to process visitor transactions. We linked nine additional merchant accounts to lidlorg[.]com via overlapping use by other scam e-commerce domains within the network.
| Merchant Name | Acquirer BIN | MCC | Date First Seen | Date Last Seen | Linked Scam Domains |
|---|---|---|---|---|---|
| AKRU KERAMIK GMBH | 264431 | 5719 | 2025-04-30 | 2025-04-30 | 1 |
| ANT*ONLINE E-COMMERCE STO | 270514 | 5631 | 2025-04-09 | 2025-04-09 | 1 |
| BALSAMIC | 270522 | 5661 | 2025-04-01 | 2025-04-09 | 2 |
| CLOTHWEARABLY | 271109, 024440 | 5691 | 2025-02-25 | 2025-03-07 | 11 |
| LMS AESTHETICS | 230230 | 5719 | 2025-04-23 | 2025-04-30 | 3 |
| MYCOZYBABIES | 271109, 024440 | 5641 | 2025-04-16 | 2025-04-26 | 5 |
| ONCLOTHESSHOES | 875516 | 5311 | 2025-04-23 | 2025-04-30 | 5 |
| PETHOUSEN LLC | 230509 | 5995 | 2025-04-19 | 2025-04-30 | 3 |
| REFINEDHAT | 271109, 024440 | 5691 | 2025-04-14 | 2025-04-23 | 4 |
| YSP*CLOTHINGGSHOP | 020608 | 5621 | 2025-03-04 | 2025-04-19 | 9 |
| YSP*NIHILSTOOL | 020608 | 5311 | 2025-03-26 | 2025-04-19 | 9 |
| YSP*QHWLKJSHOP | 020608 | 5621 | 2025-02-25 | 2025-04-26 | 25 |
Table 1: All transactions with merchant accounts linked to lidlorg[.]com are likely to be fraudulent (Source: Recorded Future)
Note that inaccurate associated merchant URL data suggests that threat actors likely use merchant accounts within this group for transaction laundering. For example, merchant data indicates that PETHOUSEN LLC is associated with pethousen[.]com rather than the three scam domains we linked it to (biliability[.]com, dknyonlineuk[.]com, outletmalleu[.]shop). Inaccurately associated merchant URLs often indicate that a merchant is engaging in transaction laundering.
Transaction laundering allows threat actors to conceal high-risk or illegal activity by processing payments for an entity, goods, or services unknown to the merchant’s acquiring bank or payment provider. While the transactions are disguised as low-risk or legitimate purchases, they are often transactions for illegal activities. In this sense, all purchase scam transactions that defraud victims are inherently a form of transaction laundering.
It is unclear whether the scam network identified in this report is controlled by a single threat actor or various threat actors acting in concert. Merchant account abuse for purchase scams frequently overlaps between networks of linked domains, as shown in Figure 2. While merchant accounts dispersed throughout scam networks network can have similarities that suggest a common origin or operator, the networks of scam domains linked to the merchant accounts are often distinct (for example, in their abuse of different ad platforms for propagation to victims)
Because of this, we consider the two following scenarios equally likely regarding attribution of the scam network to an operator:
- Multiple networks of scam domains operated by different threat actors may be using the same merchant accounts, whose services are rented out as part of a third-party, dark web-based “cash-out” offering.
- A single threat actor may be controlling the domain and merchant infrastructure for the entire network, intentionally rotating the domain/merchant combinations in an attempt to obscure attribution.
An ecosystem of illicit dark web services likely supports fraud-focused threat actors. These threat actors leverage third-party services for a variety of scam use cases, including the following:
- Fraud-based malvertising services: Threat actors organize illicit advertising services by compromising advertiser accounts for online ad platforms or by purchasing advertising campaigns using stolen financial data.
- “Cash-out” services: Threat actors purvey merchant accounts under their control to other threat actors to monetize stolen card data.
- Traffic services: Threat actors drive traffic to artificially boost malicious advertisements, including for scam websites, in search results. Alternatively, they partner with cash-out service providers to monetize existing victim traffic to scam domains.
Card issuers and merchant acquirers with access to merchant data can likely leverage merchant analysis for threat actor attribution of this scam network. Commonalities in merchant registration would likely indicate that the accounts are operated by a single threat actor, whereas discrepancies would indicate that the accounts are operated by various threat actors. Identical company data is an example of a commonality that we would expect to see in linked merchant accounts operated by a single threat actor.
Note that since scam domains are easier to acquire and less resilient to detection and mitigation than merchant accounts (and therefore more expendable as infrastructure), we consider domain analysis less likely to enable threat actor attribution of this scam network.
Mitigations for Fraud Prevention
Purchase scams present financial fraud risks to card issuers and compliance risks to merchant acquirers, especially in cases where linked scam merchant accounts are also abused to support transaction laundering activity. To reduce these risks, apply the mitigation strategies described below.
Card Issuers
- To prioritize fraud prevention over potential customer friction, immediately decline transactions with the identified scam merchant accounts and track customer card accounts that have transacted with the merchant for additional fraud signals before taking action.
- Escalate the fraud risk score of customer accounts that attempt transactions with the merchants or flag the account for additional review.
- Consider the presence of additional fraud signals on flagged accounts as a high-confidence basis to reissue the customer card or apply other remediations.
- To minimize customer friction, assess transaction data within your cardholder portfolio with the identified scam merchant accounts before taking action against either the merchant accounts or customer card accounts.
- Bucket all customer transactions with the identified merchants.
- Determine a fraud incidence threshold in accordance with your organization’s risk tolerance. This threshold should be higher than the baseline fraud incidence rate observed across your portfolio.
- If customer transactions within the bucket exceed the fraud incidence threshold, automatically block all customer transactions with the identified merchant accounts and consider card reissue.
- Analyze linked merchant domains to identify other likely fraudulent merchant accounts operated within the scam network. Card network acquirer data lookup APIs may enable merchant acquirers to search for merchant accounts based on domain.
- Scan merchant acquirer BIN and MCC combinations within your merchant portfolio to identify other likely fraudulent merchant accounts registered with similar merchant data or within a short period of time. Card network APIs may enable merchant acquirers to search for merchant account registrations based on acquirer BIN and MCC.
- Flag suspected fraudulent merchant accounts for enhanced due diligence, investigation, suspension, or termination in accordance with your risk tolerance.
Merchant Acquirers
Outlook for Purchase Scam Networks
Our analysis has confirmed that the likely purchase scam network identified in this report has been operational since February 2025. Because we continue to confirm new scam domains within the group are operational, the scam operation appears to be ongoing. By extension, the scam operator will likely continue deploying new domains and online ad campaigns to support their scam activity, especially as old domains and ad campaigns are taken offline.
These new scam domains will likely use the merchant accounts identified in this report. Termination or suspension of scam merchant accounts by their acquirers is unlikely to halt all scam activity by the operator. However, this kind of remediation would almost certainly place additional time and resource demands on the scam network operator to acquire new merchant account infrastructure.
Appendix: Identified Scam Domains, Linked Merchant Accounts, and Detection Dates
The table below displays the identified scam domains, the merchant accounts linked to them, and the dates they were confirmed to be linked.
| Scam Domain | Merchant Name | Date Seen |
|---|---|---|
| adairs-store[.]shop | YSP*QHWLKJSHOP | 2025-03-20 |
| biglotsfactory[.]com | YSP*QHWLKJSHOP | 2025-03-26 |
| biliability[.]com | PETHOUSEN LLC | 2025-04-19 |
| biliability[.]com | MYCOZYBABIES | 2025-04-19 |
| boxrawstore[.]shop | REFINEDHAT | 2025-04-19 |
| bugaboo-store[.]shop | YSP*QHWLKJSHOP | 2025-03-21 |
| camper-bestsale[.]shop | YSP*NIHILSTOOL | 2025-04-09 |
| candywarehouses[.]com | YSP*NIHILSTOOL | 2025-03-26 |
| clarkseuoff[.]sa[.]com | MYCOZYBABIES | 2025-04-16 |
| deuter-eu-store[.]shop | YSP*QHWLKJSHOP | 2025-03-21 |
| discountmarkets[.]shop | CLOTHWEARABLY | 2025-03-07 |
| dknyonlineuk[.]com | PETHOUSEN LLC | 2025-04-30 |
| eccoshpedk[.]com | YSP*CLOTHINGGSHOP | 2025-03-20 |
| ecoalffashion[.]shop | YSP*CLOTHINGGSHOP | 2025-03-20 |
| ecofoodcontainers[.]shop | ONCLOTHESSHOES | 2025-04-30 |
| eu[.]goldengoosefan[.]com | ONCLOTHESSHOES | 2025-04-23 |
| eu[.]stanleys1913[.]com | YSP*CLOTHINGGSHOP | 2025-04-19 |
| eu[.]stanleys1913[.]com | MYCOZYBABIES | 2025-04-19 |
| eur[.]piinkovip[.]com | CLOTHWEARABLY | 2025-02-26 |
| factorydealseu[.]com | YSP*QHWLKJSHOP | 2025-04-09 |
| factorydealseu[.]com | CLOTHWEARABLY | 2025-02-25 |
| featherrunon[.]shop | YSP*QHWLKJSHOP | 2025-04-19 |
| filippa-k[.]shop | CLOTHWEARABLY | 2025-02-25 |
| filson-stores[.]com | YSP*NIHILSTOOL | 2025-04-09 |
| finalclearancehub[.]com | ONCLOTHESSHOES | 2025-04-26 |
| finalclearancehub[.]com | MYCOZYBABIES | 2025-04-26 |
| firelighthome[.]shop | YSP*QHWLKJSHOP | 2025-04-09 |
| flagshipsale[.]com | YSP*QHWLKJSHOP | 2025-04-02 |
| florisvanbommel-outlet[.]shop | YSP*CLOTHINGGSHOP | 2025-04-19 |
| fredperrypoloss[.]shop | MYCOZYBABIES | 2025-04-16 |
| frosttrekdown[.]shop | YSP*QHWLKJSHOP | 2025-04-09 |
| goldberghdeals[.]shop | REFINEDHAT | 2025-04-14 |
| groceryoutlet[.]ru | CLOTHWEARABLY | 2025-02-26 |
| gudrunstyle[.]com | YSP*QHWLKJSHOP | 2025-04-09 |
| guessdiscount[.]shop | YSP*CLOTHINGGSHOP | 2025-04-09 |
| hotdealsok[.]shop | YSP*QHWLKJSHOP | 2025-04-09 |
| icedcoffee[.]store | YSP*CLOTHINGGSHOP | 2025-04-09 |
| jblspeaker[.]shop | CLOTHWEARABLY | 2025-02-26 |
| joma-eu[.]shop | REFINEDHAT | 2025-04-19 |
| kenwoodappliances[.]shop | CLOTHWEARABLY | 2025-03-04 |
| kenwoodkitchen[.]shop | CLOTHWEARABLY | 2025-02-28 |
| ketersale[.]shop | YSP*QHWLKJSHOP | 2025-03-20 |
| lacoste-eu[.]com | CLOTHWEARABLY | 2025-02-26 |
| lidlmarket[.]store | YSP*QHWLKJSHOP | 2025-04-03 |
| lidlmarket[.]store | YSP*NIHILSTOOL | 2025-04-03 |
| lidlods[.]com | YSP*NIHILSTOOL | 2025-04-16 |
| lidlorg[.]com | YSP*NIHILSTOOL | 2025-04-19 |
| lidlorg[.]com | REFINEDHAT | 2025-04-19 |
| lidlorg[.]com | LMS AESTHETICS | 2025-04-23 |
| lidloutlets[.]eu | YSP*QHWLKJSHOP | 2025-02-25 |
| lidlsport[.]top | YSP*CLOTHINGGSHOP | 2025-03-04 |
| lidlstores[.]com | YSP*QHWLKJSHOP | 2025-03-18 |
| lidlv[.]com | YSP*QHWLKJSHOP | 2025-04-02 |
| networktsales[.]com | MYCOZYBABIES | 2025-04-26 |
| oakley-qc[.]shop | REFINEDHAT | 2025-04-19 |
| officialfactorysale[.]com | YSP*QHWLKJSHOP | 2025-04-01 |
| onlinedesales[.]com | YSP*QHWLKJSHOP | 2025-04-11 |
| ortovox-vip[.]shop | YSP*QHWLKJSHOP | 2025-03-20 |
| outletmalleu[.]shop | PETHOUSEN LLC | 2025-04-30 |
| outletmalleu[.]shop | LMS AESTHETICS | 2025-04-30 |
| outletmalleu[.]shop | AKRU KERAMIK GMBH | 2025-04-30 |
| parkside-tool[.]com | BALSAMIC | 2025-04-09 |
| parksideamonlini[.]shop | CLOTHWEARABLY | 2025-02-27 |
| perfectfoodstorage[.]shop | CLOTHWEARABLY | 2025-02-28 |
| physicalant[.]com | REFINEDHAT | 2025-04-23 |
| physicalant[.]com | LMS AESTHETICS | 2025-04-23 |
| pnjeduewmj[.]com | CLOTHWEARABLY | 2025-02-26 |
| pocketchicvip[.]shop | YSP*QHWLKJSHOP | 2025-04-11 |
| sale-rapha[.]com | YSP*NIHILSTOOL | 2025-03-26 |
| sale-vivobarefoot[.]com | YSP*NIHILSTOOL | 2025-04-09 |
| smecmc[.]com | YSP*CLOTHINGGSHOP | 2025-03-30 |
| snowpeakk[.]shop | YSP*QHWLKJSHOP | 2025-04-26 |
| sportsale-shop[.]click | YSP*NIHILSTOOL | 2025-04-16 |
| stanleys1913[.]com | YSP*CLOTHINGGSHOP | 2025-03-26 |
| tojoy[.]online | ONCLOTHESSHOES | 2025-04-25 |
| tupolevshop-eu[.]top | YSP*QHWLKJSHOP | 2025-04-11 |
| ufpro-onlines[.]shop | YSP*QHWLKJSHOP | 2025-03-11 |
| uskuiusvipstore[.]shop | YSP*QHWLKJSHOP | 2025-04-01 |
| uskuiusvipstore[.]shop | BALSAMIC | 2025-04-01 |
| uskuiusvipstore[.]shop | ANT*ONLINE E-COMMERCE STO | 2025-04-09 |
| vejadeals[.]shop | ONCLOTHESSHOES | 2025-04-23 |
| wayfairbestoffers[.]com | YSP*QHWLKJSHOP | 2025-03-26 |
| yogasports[.]shop | REFINEDHAT | 2025-04-19 |
