Langflow: CVE-2025-3248
What is CVE-2025-3248?
CVE-2025-3248 is a critical missing authentication vulnerability affecting Langflow versions before 1.3.0. Langflow is a widely used tool for building and deploying AI-powered agents and workflows. On May 5, 2025, the US Cybersecurity and Infrastructure Security Agency (CISA) also added CVE-2025-3248 to its Known Exploited Vulnerabilities (KEV) catalog. Exploiting the vulnerability can allow remote, unauthenticated attackers to send crafted HTTP requests and execute arbitrary code by abusing Python decorators and default arguments.
Given the high risk associated with this vulnerability and ongoing exploitation attempts, it is imperative to prioritize patching CVE-2025-3248 on your company’s assets to prevent unauthorized access and attackers potentially taking control of affected systems.
Insikt Group’s Assessment of CVE-2025-3248
CVE-2025-3248 arises from Langflow’s failure to implement appropriate input sanitization and execution control at the “/api/v1/validate/code” endpoint, where it insecurely uses Python’s “compile” and “exec()” function to process user-supplied code. Specifically, the vulnerability results from Langflow’s approach of validating function definitions by parsing them into an Abstract Syntax Tree (AST) and executing specific components.
The endpoint parses the user-submitted code field using “ast.parse()” to construct an AST. Langflow then uses Python’s compile function to convert the parsed AST into executable bytecode. During AST processing, Python evaluates argument default values and decorators immediately upon compilation. This evaluation occurs when the AST node representing the function is processed, not strictly during the ast.parse() step. If these components contain malicious payloads, they are executed as part of the compilation and execution phase.
Unauthenticated attackers can therefore craft malicious payloads embedded within argument defaults or decorators. Since Langflow does not enforce input validation or sandboxing, these payloads are compiled and executed within the server context, leading to remote code execution (RCE). In vulnerable versions, remote threat actors can submit specially crafted POST requests to the endpoint, potentially deploying reverse shell commands, data exfiltration scripts, or other malicious code without authentication or adequate restriction.
At the time of writing, there were 1,050 exposed Langflow instances on Shodan. However, not all of these are necessarily vulnerable as their specific versions are unknown. Additionally, cybersecurity firm Greynoise observed 361 malicious IP addresses attempting to exploit CVE-2025-3248, primarily targeting systems in the US, Australia, Singapore, Germany, and Mexico.
| Malicious IP Address | Source Location | Target Location |
|---|---|---|
| 45.33.95[.]165 | US | Germany, Singapore, UK, India, US, Netherlands, Canada, Australia, France, Bahrain, Brazil, Italy, Japan, Mexico, South Africa, South Korea, Thailand, Finland, Hong Kong, Indonesia, Israel, UAE, Belgium, Malaysia, Taiwan |
| 3.35.37[.]70 | South Korea | France, Germany, Italy, Mexico, Netherlands, US |
| 139.59.223[.]9 | Singapore | Lithuania |
| 35.221.194[.]209 | Taiwan | Germany |
| 204.216.147[.]144 | Brazil | Taiwan, Turkey |
Table 1: Example malicious IP addresses attempting to exploit CVE-2025-3248 (Source: Greynoise)
Multiple proof-of-concept (PoC) exploits were also shared on GitHub; public PoC exploits often increase the likelihood of continued active exploitation. Insikt Group did not test these PoCs for efficacy or accuracy.
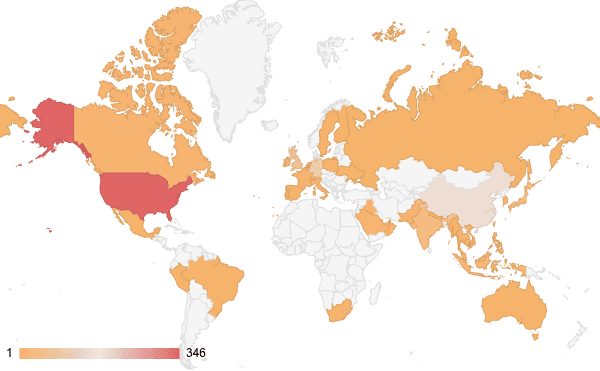
Figure 1: The majority of exposed Langflow instances on Shodan are geolocated in the US, China, Germany, Singapore, and the UK (Sources: Shodan, Recorded Future)
Recommended Actions for CVE-2025-3248
Users should upgrade to Langflow version 1.3.0. If upgrading is not possible, secure Langflow by restricting network access through a firewall and blocking public access to the “/api/v1/validate/code” endpoint. Additionally, monitor logs for suspicious POST requests on the endpoint.
How Recorded Future Can Help:
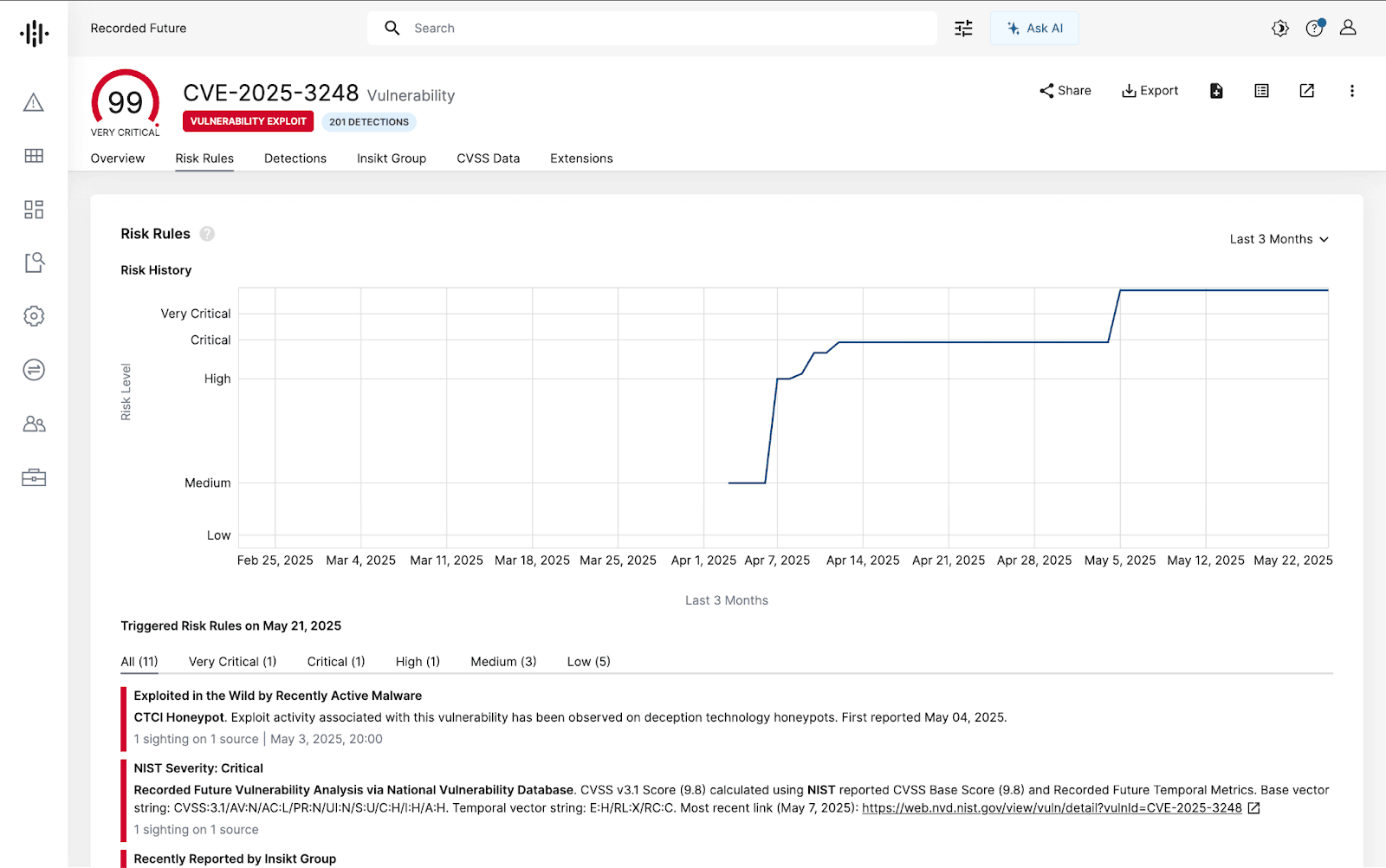
Figure 2: Triggered Risk Rules in the Vulnerability Intelligence Card for CVE-2025-3248 in Recorded Future (Source: Recorded Future)
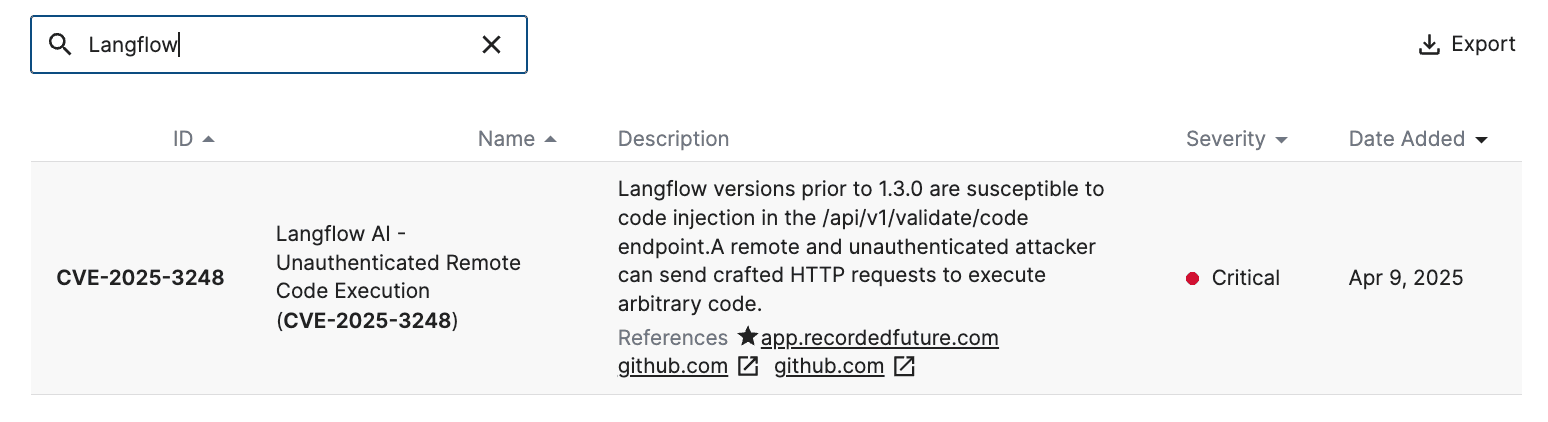
Figure 3: Signature for CVE-2025-3248 in Recorded Future Attack Surface Intelligence® (Source: Recorded Future)
About Insikt Group:
Recorded Future’s Insikt Group threat research team is comprised of analysts, linguists, and security researchers with deep government and industry experience.
Insikt Group publishes threat intelligence to the Recorded Future analyst community in blog posts and analyst notes.
