Key Findings – Q2 2025 Ransomware Trends
- Ransomware-as-a-Service (RaaS) group disruptions: Several major ransomware groups have disappeared, leaving a fragmented ecosystem.
- Slight decline in public victim extortion: Fewer victims were named on data leak sites this quarter, likely due to law enforcement pressure and changing attacker tactics.
- Continuous shift toward data extortion: Attackers continue moving away from encryption, focusing instead on stealing and leaking data to force payment.
- Ransomware group Qilin leads with new extortion tools: Qilin was the most active group in Q2, using innovative methods to pressure victims and boost ransom payments.
In Check Point Research’s latest Ransomware Threat Intelligence Report, we break down how the ransomware ecosystem is rapidly transforming. This quarter’s shift includes AI-generated malware, collapsing trust in decryption, affiliate-powered cartels, and a fragmented threat landscape that’s harder than ever to track.
Here’s what every security leader should know now and why ransomware is still one of the most profitable and fastest-moving corners of the cyber crime world.
AI-Powered Ransomware Is No Longer Theoretical
In 2025, ransomware groups aren’t experimenting with AI, they’re operationalizing it.
Earlier this year, Check Point Research observed real-world campaigns using generative AI for phishing content, code obfuscation, and victim impersonation. AI is acting as a force multiplier for cyber criminals, removing barriers to entry and reducing reliance on high-skill developers.
We’re seeing AI- Supported negotiations and innovative services
The ransomware group known as Global Group (also called El Dorado or Blacklock) advertises “AI-powered negotiation support” as part of its Ransomware-as-a-Service (RaaS) offering. This likely helps attackers refine their negotiation tactics to extract higher ransom payments.
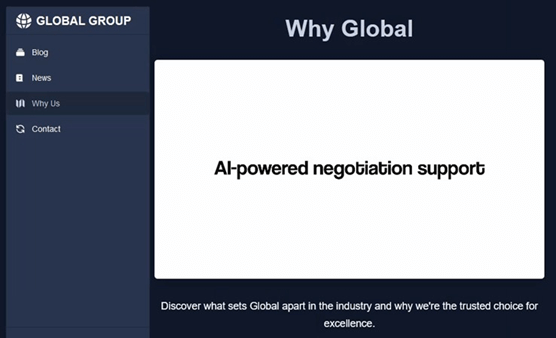
Figure 1: Global Group AI-supported negotiations
Experts believe these AI tools include:
- Bots that personalize ransom communications based on victim responses.
- AI-generated messages designed to be more persuasive or threatening.
- Psychological profiling to apply strategic pressure on decision-makers.
In Q2, Qilin also emerged as a dominant actor deploying novel extortion tools and services designed to intensify pressure on victims and maximize payouts. These include offering legal assistance to review the stolen data, assess potential regulatory violations in the victim’s jurisdiction, and prepare documentation for submission to relevant authorities such as tax agencies, law enforcement, or regulatory bodies like the FBI.
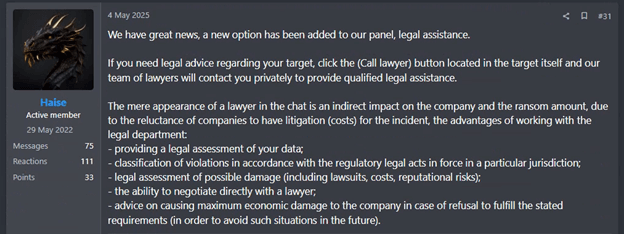
Figure 2: Qilin promoting new extortion tools on the Ramp forum
These advanced tactics raise the bar for defenders, who must adopt equally intelligent detection and response capabilities.
Cartels, Not Gangs: Ransomware-as-a-Brand
The business of ransomware is professionalizing and decentralizing.
The group DragonForce has pioneered a shift and are calling themselves a “ransomware cartel model.” Unlike traditional ransomware-as-a-service (RaaS) operations where affiliates follow a central playbook, DragonForce enables affiliates to operate semi-independently, essentially running their own campaigns, choosing their own targets, and customizing extortion tactics.
Key elements of the cartel model:
- White-label tooling: Affiliates gain access to DragonForce’s advanced ransomware builders, leak site infrastructure, and encryption mechanisms.
- Brand licensing: Attacks carry the DragonForce name, giving them immediate notoriety and fear value, even if core operators weren’t directly involved.
- Operational independence: This setup spreads risk while increasing reach, making takedowns harder and attribution murkier.
What sets DragonForce apart is also its strategic emphasis on branding and visibility, most notably through its newly established partnership with Ramp, the largest underground ransomware forum.
Figure 3: DragonForce’s logo integrated into the Ramp forum logo
Ransomware now reflects legitimate tech practices, adopting what seems like a franchise-style approach.
Think Low Payment Rates Are a Win? Think Again
For the first time, global ransomware payment rates have dropped by 25–27% according to Coveware. So, what changed?
Drivers behind the drop:
- Improved resilience: More organizations are investing in backups, segmentation, and incident response which gives them the confidence to say no to ransom demands.
- Distrust in attackers: Victims increasingly doubt that paying will result in working decryption keys or data deletion.
- Policy pressure: Governments like the U.S. and Australia are proposing or enforcing ransom payment bans, reshaping the risk calculus.
However, ransomware is not disappearing anytime soon. Instead, attackers are constantly modifying their methods:
- Various types of triple extortion: Threats now go beyond encryption to include data theft and direct attacks on customers, employees, or partners.
- Data auctions: Stolen data is sold on leak sites or dark web auctions, monetizing breaches even without victim payment.
- Reputation attacks: Some groups launch DDoS attacks or contact media and regulators to publicly pressure victims into paying.
The game is shifting from encryption for ransom to extortion by any means necessary.
Fragmentation After Collapse: The New Ransomware Normal
Ransomware dominance is no longer concentrated in a few groups. Instead, we’re seeing ecosystem fragmentation, and that’s a major challenge for defenders.
In Q2 2025 alone:
- LockBit, once the most prolific RaaS group, suffered additional operational setbacks and lost affiliates.
- RansomHub, another top-tier group, reportedly shut down.
- Cactus and other mid-tier groups have gone dark or splintered into smaller offshoots.
But instead of a decline in ransomware activity, we’re seeing a rise in new or rebranded actors with many reusing leaked codebases and tools but deploying them with greater stealth.
What this means:
- Attribution is harder: With blurred lines between groups and recycled malware, defenders can’t rely on traditional IOCs or TTPs.
- Detection is delayed: Smaller groups fly under the radar, often only surfacing after successful breaches.
- Response is slower: Law enforcement and corporate IR teams must now contend with dozens of low-signal threats rather than a few big players.
In short, the ransomware ecosystem isn’t shrinking; it’s splintering.
What Security Leaders Can Do Now
Staying ahead of ransomware in 2025 requires more than patching and perimeter defense. Based on our intelligence, we recommend:
- Adopt a connected security architecture that integrates endpoint, network, and identity protection, especially across hybrid and multi-cloud environments.
- Deploy anti-phishing at scale, including user awareness, email scanning, and behavioral analytics that can detect AI-generated lures.
- Use deception and threat hunting to expose affiliate activity and lateral movement early in the attack chain.
Segment your backups and test recovery regularly. Don’t assume immunity based on policy or past success.
Get the Full Ransomware Report
This blog offers just a snapshot of today’s ransomware landscape. For in-depth actor profiles, AI-driven tactics, geopolitical insights, and practical defense strategies, download the full Check Point Research Ransomware Intelligence Report.
