Key findings :
- A critical zero-day vulnerability (CVE-2025-53770 ) in SharePoint on-prem is actively being exploited in the wild.
- Dubbed “ToolShell,” the campaign enables unauthorized access to on-prem SharePoint servers, posing a serious risk to corporate environments
- Check Point Research identified the first signs of the exploitation on July 7th.
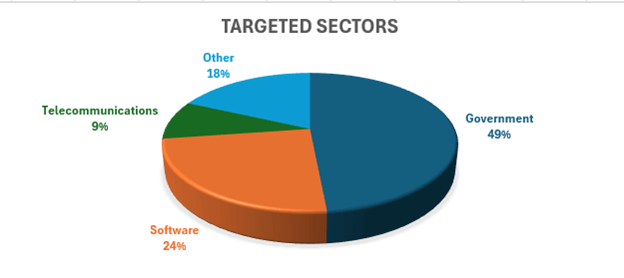
- Since then, we’ve confirmed dozens of compromise attempts across government, telecommunications, and software sectors in North America and Western Europe.
- Alarmingly, we see that the attackers also leverage known Ivanti Endpoint vulnerabilities throughout the campaign.
A critical zero-day SharePoint remote code execution (RCE) vulnerability, tracked as CVE-2025-53770 and nicknamed “ToolShell,” is currently under active exploitation. This vulnerability affects on-premise Microsoft SharePoint servers, allowing unauthenticated attackers to gain full access and execute arbitrary code remotely. Despite public guidance from Microsoft and an alert from CISA, a full security patch is not yet available.
What did Check Point Research find?
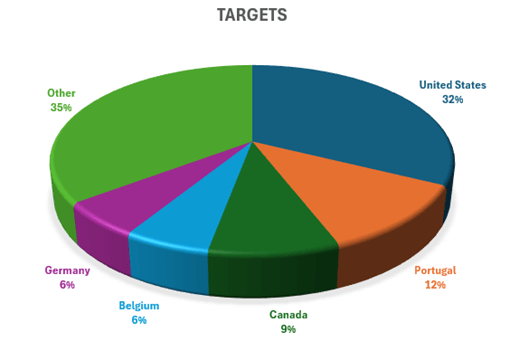
Check Point Research found that the first exploitation attempts were observed on July 7th. The target of the attack is a major Western government. The attacks only intensified on July 18th and 19th, using infrastructure tied to the following IP addresses:
- 104.238.159.149
- 107.191.58.76
- 96.9.125.147
One of these IPs was also associated with exploitation attempts against a related Ivanti EPMM vulnerability chain (CVE-2025-4427 and CVE-2025-4428).
The attack vector involves a custom webshell that parses parameters from VIEWSTATE payloads, enabling insecure deserialization attacks. Targeted sectors include:
- Government
- Software
- Telecommunications
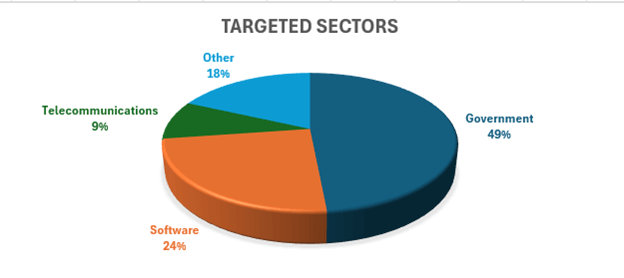
The primary geographies impacted are North America and Western Europe, especially organizations running on-prem SharePoint environments.
What does it mean for defenders and corporations?
This exploitation campaign reinforces the critical need to monitor and defend legacy and on-premise infrastructure. Threat actors are rapidly leveraging unpatched SharePoint vulnerabilities and chaining exploits like CVE-2025-53770 with older flaws such as CVE-2025-49706 to gain initial access and escalate privileges.
This is yet another case of zero day SharePoint exploitation being used in targeted attacks against sectors that manage sensitive data and critical systems.
Recommendations for Defenders
To reduce risk from CVE-2025-53770 and related threats:
- Ensure that your Anti-Malware Scan Interface is enabled.
- Rotate SharePoint Server ASP.NET machine keys.
- Deploy Harmony Endpoint to block post-exploit activities on the server.
- If applicable, limit access to the SharePoint Server from the Internet using Private Access tools.
- Update Quantum Gateway IPS Package 635254838 and ensure that the protection is set to Prevent and inspect the traffic of your SharePoint servers.
If you see signs of suspicious activity, contact Check Point Incident Response.